ISO 27001 Certification
🔐 ISO/IEC 27001 Certification in 30 Days*
🛡️ Protect Information & Build Customer Confidence
- Secure confidential business data
- Prevent data breaches and cyber risks
- Ensure compliance with privacy laws
- Build trust with clients and regulators
- 100 % guarantee — we don’t get paid until you’re certified
🎁 Limited Time: Get a Free 2-Hour Training & Awareness Session with Certificates — for a Group of 5!
🛡️ Benefits of ISO 27001 Certification
🛡️ Data Protection
Secures digital and physical data against breaches and unauthorized access.
⚖️ Legal Compliance
Meets global data-privacy regulations such as GDPR and ISO/IEC frameworks.
🚨 Risk Management
Identifies and mitigates data-security vulnerabilities proactively.
🔍 Integrity & Confidentiality
Ensures your organization maintains data reliability, accuracy, and confidentiality.
🤝 Customer Trust
Enhances your reputation and client confidence through secure data-handling systems.
🏆 Global Recognition
Improves your standing in industries that value security and compliance.
What is ISO 27001 Certification?
ISO 27001 certification is the gold standard for Information Security, Cybersecurity and Privacy Protection – Information Security Management System (ISMS) in a time of growing cyber threats, data breaches, and regulatory pressures. ISO 27001 is an internationally recognized standard for Information Security Management System (ISMS). ISO 27001 was first published in 2005 and last revised in the year 2022.
To secure ISO 27001 certification standards, a firm should undergo an audit process conducted by any renowned Certification Body, such as SIS Certifications. SIS is accredited and recognized by IAS and UAF. SIS Certifications possess all essential resources, required to conduct an effective audit of management systems across organizations.
The CB equipped with a team of over 500 auditors and technical experts spanning over 30 industries in over 50 countries. SIS can conduct audits of different standards. Moreover, it delivers hybrid audit services, where one person is present onsite whereas other members handle the audit remotely using IC Tools. In addition to this, auditors of SIS can speak multiple languages, thus, they can communicate in English as well as local languages, ensuring better understanding during the audit process.
Applicability of ISO 27001 – Industry Wise Benefits
| Industry | Information / Assets Protected | Benefits of ISO 27001 Certification |
|---|---|---|
| Manufacturing | Design data, blueprints, product specifications, and supply chain information. | Helps manufacturing organizations protect sensitive designs, process data, and innovative ideas from theft, tampering, and cyberattacks. |
| Banking & Financial Services | Financial records, customer credentials, transaction details, and sensitive financial data. | Provides a reliable and flexible framework to safeguard valuable customer data, reduce fraud risks, and meet regulatory and compliance expectations. |
| Construction | BIM models, project plans, designs, contracts, and digital drawings. | Helps construction companies comply with ISMS requirements, protect critical project information, and maintain smooth operations and continuity. |
| Healthcare | Patient records, diagnostic reports, medical history, and treatment data. | Reduces data breaches, protects confidential medical information, and strengthens patients’ trust in healthcare service providers. |
| IT and Software | Client code, application data, intellectual property, and cloud-based information. | Helps tech companies stay ahead of cyber threats, system malware, and data breaches by implementing strong information security controls. |
| Pharmaceuticals | Research findings, clinical trial data, formulations, and medical databases. | Enables pharmaceutical companies to secure critical medical and research data, protect competitive advantage, and maintain consumer trust. |
| Telecommunications | Network configurations, customer usage data, communication logs, and service data. | Allows telecom organizations to establish secure network channels, manage information security risks, and ensure uninterrupted and trusted services. |
| Logistics & Transportation | Shipment data, routing information, customer details, and tracking records. | Helps logistics companies secure sensitive logistics data, avoid data manipulation, and enhance customer confidence in delivery services. |
| Oil & Gas / Energy | Operational technology (OT) data, digital and cloud-based operational information, SCADA data. | Shields critical digital and cloud data, prevents costly breaches, and builds lasting trust in the Oil & Gas / Energy sector. |
| Automotive | Design data, testing results, connected vehicle data, and supply chain information. | Protects automotive organizations from cyber threats, supports secure collaborations, and complements TISAX by enhancing prototype and data protection. |
| Public Sector / Government | Citizen data, government records, policy documents, and confidential information. | Provides a comprehensive framework to manage information security risks, protect sensitive citizen data, and build public confidence in government services. |
| Finance & Insurance | Customer financial information, policy records, claims data, and risk profiles. | Enables finance and insurance companies to implement smart risk management strategies, keep financial and customer data safe, and comply with regulatory requirements. |
📑 Table of Contents – ISO/IEC 27001 Certification
- Benefits of ISO/IEC 27001 Certification
- What is ISO/IEC 27001 Certification?
- Apply for ISO/IEC 27001 Certification
- Why is ISO/IEC 27001 Certification Important?
- Key Benefits of ISO/IEC 27001 Certification
- Major Changes in ISO/IEC 27001:2022
- Requirements of ISO/IEC 27001 Compliance
- How to Maintain ISO/IEC 27001 Certification
- Certification Process – ISO/IEC 27001
- ISO/IEC 27001 FAQs
What is an Information Security Management System (ISMS) ?
An Information Security Management System (ISMS) is a set of rules that are designed to secure the information stored in digital form by identifying the risks to your information infrastructure. It also aims at meeting the expectations of your stakeholders by implementing controls and continually improving the Information Security Management System (ISMS) according to the changing market standards. These rules can be documented in the form of records of policies and processes or can be established with non-documented technologies.
ISO 27001 is one of the internationally recognized standards for information security management system (ISMS). The main focus of ISMS is on information security, but cybersecurity and privacy protection also feature in its scope. An organisation’s focus to maintain its assets, repelling against cybersecurity attacks, and ensuring privacy laws can be shown by its ISO 27001 certification.
Implementation of ISO 27001 Certification for an Organization
The ISO 27001 standard provides the framework for an effective Information Security, Cybersecurity and Privacy Protection — Information Security Management System (ISMS). It sets out the policies and procedures needed to protect your organization. It includes all the risk controls (legal, physical and technical) necessary for robust IT security management.
Any organization, whatever its size, sector or shareholder structure, can implement ISO 27001 certification standard . The standard’s authors were all experts in the field of IT security management. As such, it provides an internationally accepted framework for implementing effective information security management.
Why is ISO 27001 Certification so important ?
The business benefits from ISMS ISO 27001 certification are considerable. Not only do the standards help ensure that a business’ security risks are managed cost-effectively, but the adherence to the recognised standards sends a valuable and important message to customers and business partners: this business does things the correct way. Information Security, Cybersecurity and Privacy Protection — Information Security Management System (ISMS) ISO 27001 is invaluable for monitoring, reviewing, maintaining and improving a company’s information security management system and will unquestionably give partner organisations and customers greater confidence in the way they interact with your business.
Who Should use the ISO 27001 Certification?
The scope of ISO 27001 Certification is not limited to IT industries. With the advent of the digital era, every organization began to maintain a soft copy of their records. Rampant usage of the internet has led to the rise of data. In such a scenario, any breach or loss of data may cost the organization a heavy sum. Thus, it is important for all kinds of organizations- big or small- to maintain a robust Information Security, Cybersecurity and Privacy Protection — Information Security Management System (ISMS) for data protection. This helps in gaining the trust of clients and customers that their data is safe and secured.
Steps to Get ISO 27001 Certified
There are a few steps you need to take in order to get your organization ISO 27001 certified.
1. The first step is to develop your organization’s information security management system (ISMS). This system should be tailored to the specific needs of your organization and include all aspects of information security, from Policies and Procedures to Risk Management.
2. Once your ISMS is developed, you will need to have it audited by an accredited certification body. This audit will ensure that your ISMS meets all the requirements of the ISO 27001 standard.
3. Once you have passed the certification audit, you will be issued an ISO 27001 certificate, which is valid for three years. In order to maintain your certification, you will need to undergo annual surveillance audits and recertification audits every three years.
Factors Affecting ISO 27001 Certification Cost
Several factors affect ISO 27001 Certification cost. Here are some of the key considerations:-
- Size of the Organization: Implementing and maintaining an Information Security Management System (ISMS) that complies with ISO 27001 often takes more time and resources for larger organizations with complex structures and processes. This may increase the cost.
- Complexity of the Business: The cost may vary depending on the size of the firm, the number of locations, and the type of information system employed. More thorough audits and controls may be necessary for organizations with more complicated operations.
- Maintenance Costs: Costs associated with maintaining ISO 27001 compliance include recurring audits, revisions to policies and procedures, and continuing improvements.
- Location of the business: The cost of the ISO 27001 Certification may vary depending on the company’s location. Depending on where the company is located, different Certifying Bodies may have different fee structures, and travel costs for Auditors may also change.
- Scope of the Certification: The range of information assets and business processes that an Information Security Management System (ISMS) covers is referred to as the certification’s scope. The cost of certification rises as the scope gets wider as it takes more time and resources to evaluate the Information Security Management System (ISMS).
Ways to Reduce the Cost of ISO 27001 Certification for any Business
Perform a Gap Analysis prior to beginning the Certification process: The first step in figuring out how much your organization complies with the requirements of the ISMS ISO 27001 standard is to conduct a gap analysis. It will point out areas that need advancement and assist you in concentrating on certain controls to implement. You may save money by not introducing controls that are unnecessary or already in place by performing a gap analysis.
Implement processes to promote ongoing improvement: Your organization will be able to maintain the efficacy of your information security management system (ISMS) and find areas for improvement by putting continuous improvement methods into place. The ISO 27001 ISMS Standard’s essential principle of continuous improvement is a requirement for retaining Certification. By avoiding expensive re-certification audits and lowering the requirement for costly corrective measures, can assist you in lowering certification expenses.
Choose a Certification Body wisely: You may save time and money by choosing an ISO Certification Body that is recognized by an acknowledged accreditation body and has experience in your industry. Accredited Certification Bodies are obligated to follow certain guidelines, and their auditors are trained to be impartial and unbiased. Making the right decision in choosing a Certification Body will help you avoid the costs of switching Certification bodies or dealing with poor-quality Audits.
How to Maintain ISO 27001 Certification?
There are a few key things to keep in mind when working towards and maintaining ISO 27001 certification :-
1. Keep your documentation up to date and accurate. This includes your security policy, risk assessment, and any procedures or controls you have in place.
2. Make sure all employees are aware of the importance of compliance and security, and that they understand their roles and responsibilities in relation to ISO 27001.
3. Regularly review your security posture and make sure you are taking steps to address any identified risks.
4. Maintain an incident response plan so you know how to deal with any potential security breaches.
By following these tips, you can help ensure that your organization remains compliant with ISO 27001 and keeps its certification status.
Advantages of ISO 27001 Certification
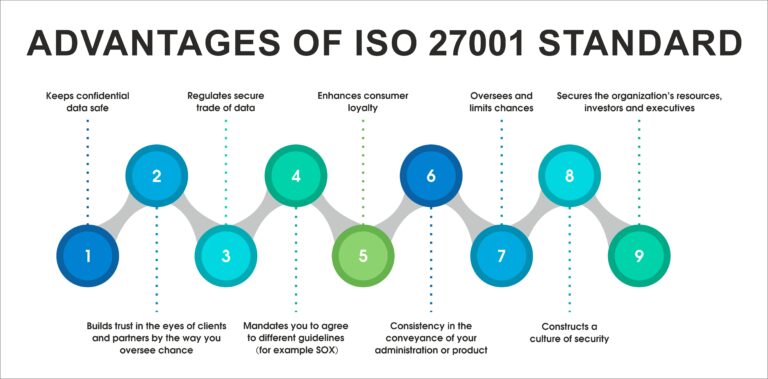
What are the 5 key benefits of ISO 27001 Certification?
There are many benefits to achieving ISO 27001 certification, including :-
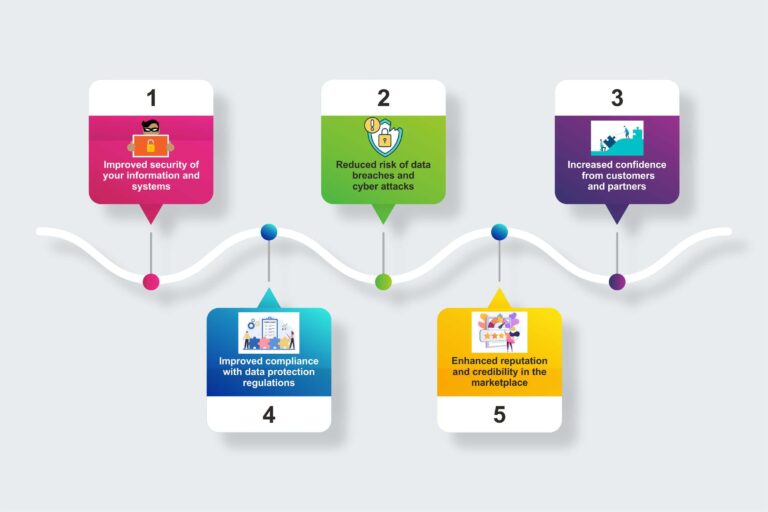
As the world becomes increasingly digital, the need for robust information security grows. ISO 27001 is the international standard that provides a framework for an effective Information Security Management System (ISMS). ISO 27001 demonstrates that your organization takes information security seriously and is committed to protecting your data.
Achieving certification requires a comprehensive approach to information security, covering people, processes, and technology. The ISO 27001 benefits of certification will be felt across your entire organization, from the boardroom to the frontline. Your customers and partners will have increased confidence in your ability to keep their data safe, while you reap the rewards of reduced risk and improved compliance.
List of Information Security Threats and Vulnerabilities in ISO 27001
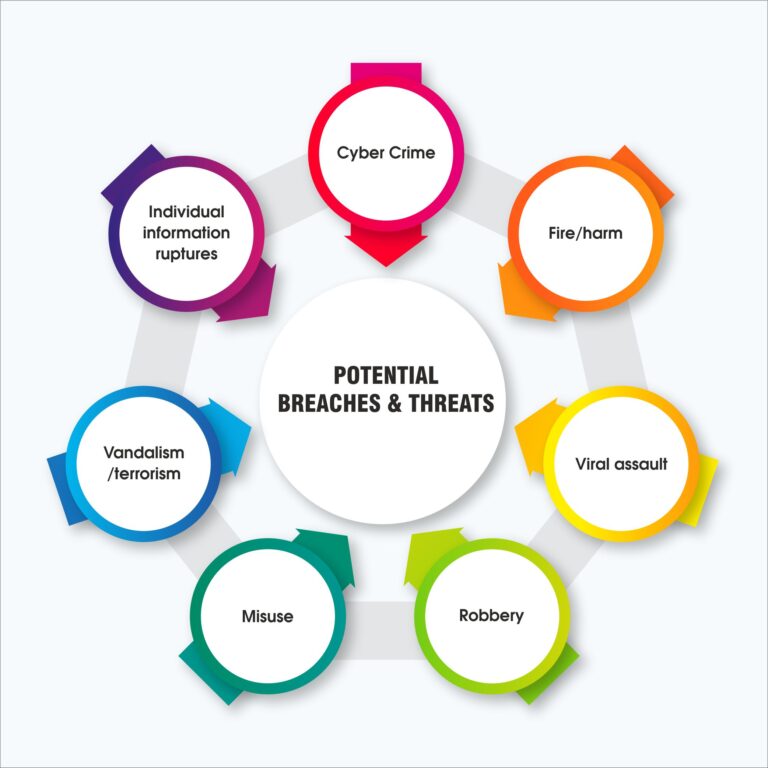
What are the major changes in ISO 27001 Certification Standards?
Some of the main new updates of ISO/IEC 27001:2022 include a major change of Annex A, minor updates of the clauses, and a change in the title of the standard.
The latest version of ISO/IEC 27002 has been published at the beginning of 2022, and its latest changes have also impacted ISO/IEC 27001.
Requirements of ISO 27001 Certification
Context to the Organization
Existing – Context to the Organization – It requires an organization to define the scope of ISMS and identify all the internal and external issues related to its information security and the expectations of the interested parties.
New – Context to the Organization – An organization must understand the context of the organization and define its scope to establish an effective Information Security Management System. The latest update requires an organization to identify only the relevant requirements, which will be addressed through the Information Security Management System (ISMS).
Planning
Existing – It requires an organization to define its information security objectives based on the risk assessment and implement appropriate controls listed in Annex A. It determines plans and actions to address risks and opportunities and prepares a Statement of Applicability (SoA).
New – An organization requires defining its information security objectives based on the risk assessment and implementing appropriate controls listed in Annex A. It also requires documenting the available information and determining plans and actions to address risks and opportunities and preparing a Statement of Applicability (SoA).
Support
Existing – It focuses on the competence of personnel, resources, people, and infrastructure and establishes sound communication, including external and internal, to establish a sound ISMS. It provides necessary training to the employees and requires documenting information related to information security.
New – It aims to enhance the competence of personnel, resources, people and infrastructure and establishes sound communication, including external and internal, to establish a sound ISMS. An organization shall focus on “how to communicate” rather than “who will communicate.”
Operation
Existing – This clause works in line with Clause 6 and focuses on the execution of all the plans and processes. It outlines the outcomes of the risk assessment and requires maintaining all the related documents. It focuses on implementing risk assessment and treatment plans to establish an efficient Information Security Management System (ISMS).
New – This clause works in line with Clause 6. The latest update replaces the requirements to plan how to achieve ISO 27001 compliance for information security objectives with establishing criteria for processes to implement the actions identified in the planning clause. An organization must control its external processes, products, and services related to the Information Security Management System (ISMS).
Performance Evaluation
Existing – It requires an organization to monitor, measure, analyze and evaluate the ISMS to ensure its effectiveness and efficiency. It evaluates the organization’s performance to the defined objectives. This ISO 27001 clauses list also requires an organization to conduct internal audits to review its Information Security Management System (ISMS).
New – An organization shall adopt comparable and reproducible methods to monitor, measure, analyze, and evaluate the ISMS to ensure its effectiveness and efficiency. It evaluates the organization’s performance to the defined objectives. This is 27001 clauses and controls also require an organization to conduct internal audits to management review to measure its Information Security Management System (ISMS) and make necessary changes to meet the needs and requirements of interested parties.
ISO 27001 Clauses and Controls – Annex A Security Control
| New – The number of Annex A Security Controls is reduced from 114 to 93 controls. These controls are further divided into 4 themes rather than 14 domains.
The new ISO 27001:2022 version introduces 11 new controls to the Annex A Security Control list. These new controls are:-
| Existing – ISO 27001 Annex A Controls or ISO 27001 controls . They are grouped into 14 domains. These are:-
|
Read more about – A Step By Step Guide to ISO 27001 Annex A Controls
PDCA Cycle
- Plan – to think that what do we need to achieve in our organization
- Do – to execute a planned action which will help us achieve the required objective
- Check – monitor against the standards) (policies, objectives, requirements)
- Action – finally implementing what has been rechecked.
How SIS Certifications can help you
ISO 27001 certification is a great way to show your commitment to security and demonstrate that you have implemented best practices. Getting certified can be a complex process, but it is well worth the effort to ensure that your organization is protected against potential threats. Our team of experts can help you navigate the certification process and ensure that you are prepared for success. Contact us today as we are leading ISO 27001 Certification Bodies in India to learn more about how we can help you get ISO 27001 certified.
ISO 27001 Frequently Asked Questions (FAQs)
Answer:
In 2022, the average global data breach cost was approximately $4.35 million, highlighting inadequate data protection strategies in many organizations. ISO 27001, part of the ISO 27000 family, provides a structured framework for implementing an Information Security Management System (ISMS). It guides organizations on how to establish, maintain, monitor, and continually improve their ISMS to protect data, documents, and other critical information assets.
Answer:
ISO/IEC 27001 is an internationally recognized standard that supports the implementation of a comprehensive Information Security Management System (ISMS). It helps organizations maintain confidentiality, integrity, and availability of information. ISO 27000, the broader series, includes best practices that strengthen and enhance information security management across the organization.
CERTIFICATION PROCESS
Ready to Get ISO Certified?
Join 500+ Global Companies that have Successfully Achieved ISO Certification with Us.
Missing Something?
We’re here to help you find exactly what you need—just let us know, and we’ll guide you in the right direction.

